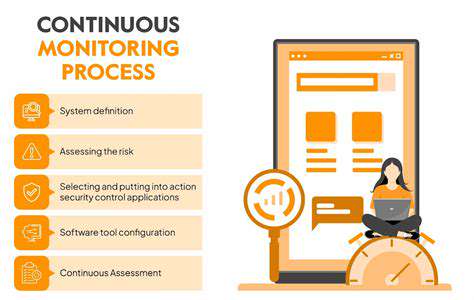
Implementing Mechanisms for Continuous Monitoring and Evaluation
Implementing Robust Security Measures
Implementing robust security measures is crucial for protecting sensitive data and preventing unauthorized access. This involves a multi-layered approach encompassing various technologies and procedures. Security measures should be carefully tailored to the specific needs and vulnerabilities of the system, considering factors like the type of data handled, the potential threats, and the regulatory environment. This proactive approach minimizes the risk of security breaches and ensures the confidentiality, integrity, and availability of the system.
A comprehensive security strategy should include strong password policies, regular security audits, and robust access controls. These measures significantly increase the resilience of the system against potential attacks. Furthermore, employee training programs are essential to educate staff about potential risks and best practices for maintaining security, thereby fostering a culture of security awareness within the organization.
Establishing Clear Access Control Policies
Establishing clear access control policies is paramount for maintaining data security and confidentiality. These policies need to define who has access to what resources and under what conditions. This is a critical step in preventing unauthorized access and misuse of sensitive information.
Strict adherence to these policies ensures that only authorized personnel can access specific data or systems. This minimizes the risk of data breaches and protects the organization's reputation and assets.
Developing Secure Data Storage Solutions
Developing secure data storage solutions is vital for safeguarding sensitive information. This includes implementing encryption technologies to protect data both in transit and at rest. Robust encryption protocols are paramount to mitigating the risk of data breaches and unauthorized access. Regular backups and disaster recovery plans are essential to ensure business continuity in case of data loss or system failures.
Implementing secure data storage solutions helps meet regulatory requirements, maintain compliance, and protect the organization from financial and reputational damage.
Implementing Regular Security Audits
Regular security audits are essential for identifying vulnerabilities and weaknesses in the system. These audits should be conducted periodically to ensure that security measures remain effective and up-to-date. This proactive approach helps to detect and address potential security threats before they can cause significant damage. Security audits should encompass various aspects of the system, including network infrastructure, applications, and data storage.
Audits should also assess the effectiveness of existing security policies and procedures, and identify areas for improvement. Thorough security audits are critical for maintaining a robust and resilient security posture.
Implementing Secure Development Practices
Implementing secure development practices throughout the software development lifecycle is critical for preventing vulnerabilities from entering the system in the first place. This involves integrating security considerations into every stage of development, from design to testing and deployment. This approach minimizes the risk of exploitable vulnerabilities being introduced during development.
Secure development practices should be prioritized and incorporated into the overall development process. This will help to reduce the likelihood of security breaches and ensure the long-term security of the system.
Monitoring and Responding to Security Threats
Continuous monitoring of system activity and proactive responses to potential security threats are crucial for maintaining a strong security posture. This involves employing intrusion detection systems and security information and event management (SIEM) tools to detect anomalies and suspicious activity. Monitoring and responding to threats in real-time is vital for minimizing the impact of security incidents.
A well-defined incident response plan is essential for effectively managing and mitigating security incidents. This plan should outline procedures for detecting, analyzing, containing, and recovering from security breaches, ensuring minimal disruption and damage.