Understanding Defense Mechanisms
Defense mechanisms are unconscious psychological strategies employed by individuals to cope with anxiety and protect their self-esteem. They operate automatically and often unconsciously, helping to manage difficult emotions and situations. Understanding these mechanisms is crucial for self-awareness and personal growth, as recognizing their presence can lead to more constructive ways of handling challenging emotions and experiences. These strategies, while often helpful in the short term, can sometimes become maladaptive if relied upon excessively. Ultimately, understanding their function and potential drawbacks is key to developing healthier coping mechanisms.
Defense mechanisms are a normal part of the human experience, offering a temporary buffer against overwhelming emotions. They can be likened to a safety net, protecting us from feelings of vulnerability, hurt, or shame. However, it's important to remember that excessive or inappropriate use of these mechanisms can lead to difficulties in relationships and overall well-being. A deeper understanding of these strategies allows for a more nuanced perspective on personal responses to stress and emotional challenges.
Types of Defense Mechanisms
There are various types of defense mechanisms, each serving a unique purpose in managing anxiety and stress. Some common examples include repression, where painful memories or thoughts are pushed out of conscious awareness, and denial, where individuals refuse to acknowledge unpleasant realities. Projection involves attributing one's own unacceptable feelings or impulses to someone else. These are just a few of the many defense mechanisms that can play a role in shaping our thoughts and behaviors.
Another example is displacement, where emotions are redirected from a threatening source to a less threatening one. For instance, anger directed at a boss might be channeled into frustration towards a family member. Rationalization involves creating logical-sounding explanations for unacceptable behaviors or feelings, often to justify actions that cause discomfort. Recognizing these different mechanisms can be valuable in understanding the motivations behind our own actions and those of others.
Further exploration of these mechanisms can lead to a deeper understanding of the complexities of the human psyche. Understanding how we use these strategies can lead to more self-awareness and facilitate healthier coping mechanisms in the long run.
Overcoming Reliance on Defense Mechanisms
While defense mechanisms are a natural part of coping, becoming overly reliant on them can hinder personal growth and create problems in relationships. Recognizing when these strategies are being used excessively is a crucial step in moving toward healthier ways of managing stress and emotions. Therapy can provide a supportive environment for exploring these patterns and developing more constructive coping mechanisms. A trained therapist can help identify recurring patterns and teach individuals more adaptive ways of dealing with difficult emotions and experiences.
Developing emotional intelligence is crucial in reducing reliance on defense mechanisms. This involves understanding and managing one's own emotions and recognizing the emotions of others. Practicing mindfulness and self-reflection can help individuals become more aware of their emotional responses and develop strategies to manage them effectively without resorting to defense mechanisms. This process, while challenging, ultimately leads to greater emotional well-being and healthier relationships.
Working to confront and address underlying anxieties, rather than avoiding them, is an essential aspect of overcoming reliance on defense mechanisms. Facing these issues head-on, with the support of a therapist or counselor, can lead to a greater sense of personal growth and well-being.
A slow and steady transition is crucial to preventing digestive upset in your pet. Instead of abruptly switching your pet to the new food, gradually introduce it over a period of several days. This gradual introduction allows your pet's digestive system to adjust to the new ingredients and nutrients, minimizing any potential discomfort or illness. Start by mixing a small portion of the new food with a portion of their current food, gradually increasing the proportion of the new food each day until they're entirely on the new formula.
The Importance of Continuous Monitoring and Adaptation
Understanding the Evolving Threat Landscape
Adversarial machine learning attacks are not static; they're constantly evolving. This means that a model trained today might be vulnerable to new attack vectors tomorrow. A critical element of robust machine learning systems is the ability to detect and respond to these dynamic threats. Continuous monitoring is essential for identifying anomalies and shifts in the data that could indicate an ongoing or emerging attack. This proactive approach allows for swift adaptation and mitigation strategies.
The sophistication of adversarial attacks is increasing rapidly, making it challenging to rely on static defense mechanisms. Researchers are continuously developing new techniques for crafting adversarial examples, pushing the boundaries of what was previously considered possible. Staying ahead of these developments requires a commitment to continuous learning and adaptation in the field of machine learning security.
Monitoring for Anomalous Behavior
A crucial aspect of continuous monitoring involves identifying patterns that deviate significantly from the expected behavior. These anomalies could be subtle changes in input data, unexpected output fluctuations, or unusual increases in error rates. By establishing baselines and thresholds for acceptable performance, we can detect deviations that signal potential adversarial activity.
Monitoring tools and techniques can be employed to track various aspects of the model's performance. This includes analyzing input features, evaluating model outputs, and measuring the model's robustness against known attack vectors. These metrics provide valuable insights into the model's vulnerability and allow for timely intervention.
Adapting Models to Counterattacks
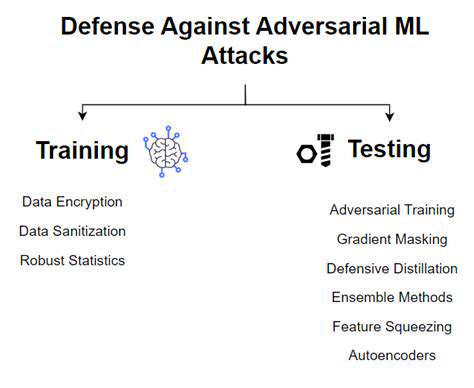
Once anomalies are identified, the next step is to adapt the model to counter the detected attacks. This might involve retraining the model with updated data that incorporates the newly discovered attack patterns. Alternatively, it could involve implementing defensive mechanisms like adversarial training or adding layers of detection to identify and filter out adversarial inputs.
The process of adaptation should be iterative and automated wherever possible. Continuous feedback loops between monitoring systems and model retraining processes are essential for maintaining a strong defense against ongoing adversarial attacks. This ensures the model remains resilient and effective even as the attacks become more sophisticated.
Implementing Robust Defense Mechanisms
Robust defense mechanisms are crucial to ensure the model's continued effectiveness in the face of adversarial attacks. This involves incorporating techniques to detect and mitigate adversarial inputs. Implementing these mechanisms requires careful consideration of the specific nature of the data and the type of attacks being targeted.
Techniques such as data augmentation, input sanitization, and output validation can be integrated into the model's pipeline. Implementing these mechanisms often involves careful analysis of the attack vectors and the specific vulnerabilities of the model to tailor the defenses accordingly. Furthermore, incorporating human oversight in the adaptation process can provide valuable insights and reduce the risk of unintended consequences.
The Role of Feedback Loops and Continuous Improvement
Continuous monitoring and adaptation are not one-time processes; they require ongoing evaluation and refinement. Establishing feedback loops that allow for the continuous assessment of model performance and the identification of new vulnerabilities is essential for maintaining a robust defense. This iterative approach allows for ongoing improvements to the model and the defense mechanisms employed.
Regularly evaluating the effectiveness of the implemented defenses and adapting them to new attack patterns is critical. This process necessitates collecting and analyzing data on the performance of the model, the nature of adversarial attacks, and the effectiveness of the implemented countermeasures. This feedback loop ensures that the system remains resilient and adaptable to the ever-changing landscape of adversarial machine learning.