Quantum Computing and Cryptography: A Complex Interplay
Quantum computing, a rapidly emerging field, promises unprecedented computational power, but its potential impact on cryptography is both exciting and deeply concerning. The fundamental principles of quantum mechanics, unlike classical physics, allow for the manipulation of quantum bits (qubits) in ways that unlock the ability to solve problems currently intractable for even the most powerful supercomputers. This inherent power, however, presents a significant challenge to the security of existing cryptographic systems, forcing researchers to develop quantum-resistant alternatives.
The relationship between quantum computing and cryptography is a complex one, requiring a nuanced understanding of both fields. Quantum algorithms, designed to exploit the unique properties of qubits, could potentially break widely used encryption methods, jeopardizing the confidentiality and integrity of sensitive data across various sectors, from finance and healthcare to national security.
The Threat to Existing Encryption Standards
Current public-key cryptography, the cornerstone of modern secure communication, relies on the computational difficulty of factoring large numbers and solving discrete logarithm problems. These problems, while seemingly intractable for classical computers, become potentially solvable with quantum computers employing Shor's algorithm. This poses a direct threat to widely used encryption standards like RSA and ECC, rendering them vulnerable to decryption by sufficiently powerful quantum computers.
Beyond RSA and ECC, other cryptographic systems, including those used for digital signatures and key exchange, are also vulnerable to quantum attacks. This vulnerability necessitates a proactive approach to developing and deploying quantum-resistant cryptography to maintain security in the face of advancements in quantum computing.
Quantum-Resistant Cryptography: A Necessary Response
The need for quantum-resistant cryptography is undeniable. The transition from classical to quantum-resistant cryptography is not simply an academic exercise; it's a critical security imperative. Researchers are actively exploring novel mathematical structures and algorithms that are resilient to attacks from quantum computers. These efforts are focused on developing new cryptographic primitives that are resistant to both classical and quantum attacks. This includes exploring lattice-based cryptography, code-based cryptography, and multivariate cryptography as promising alternatives.
The development and standardization of quantum-resistant cryptographic algorithms is a complex and time-consuming process. It requires rigorous mathematical analysis, extensive testing, and careful consideration of potential vulnerabilities. Collaboration between researchers, industry, and policymakers is essential to ensure a smooth transition to a more secure cryptographic landscape.
The Future of Secure Communication in a Quantum World
While the development of quantum-resistant cryptography is underway, the transition to a quantum-resistant future is not immediate. The timeline for widespread adoption of these new algorithms is uncertain, but it's imperative to initiate the necessary research and development efforts now. This involves investing in research and development, educating the public and professionals about the implications of quantum computing, and establishing standards and protocols for quantum-resistant cryptography.
The development of quantum-resistant cryptography will require significant investment and collaboration. This is a global challenge that demands a concerted effort from governments, institutions, and private companies to mitigate the potential risks and ensure the security of sensitive data in the face of a quantum computing revolution.
The Impact on Different Sectors
The implications of quantum computing for cryptography extend across numerous sectors. Financial institutions, governments, healthcare providers, and individuals will all be affected by the transition to quantum-resistant cryptography. The potential for breaches of sensitive data in these sectors underscores the critical importance of proactively developing and deploying quantum-resistant algorithms and systems.
The widespread adoption of quantum-resistant cryptography will require significant adjustments and upgrades in infrastructure and systems. This necessitates a strategic approach to managing the transition, ensuring that all stakeholders are prepared for the shift and that the security of critical systems remains intact.
Beyond Encryption: The Wider Implications

Beyond Encryption: Protecting Data in the Digital Age
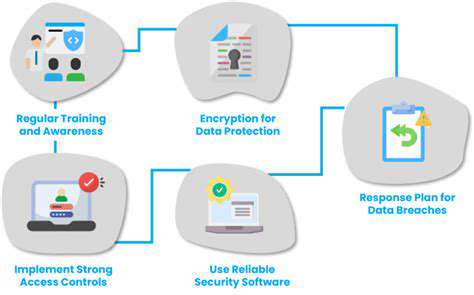
Data security is paramount in today's interconnected world, and while encryption plays a crucial role, it's only one piece of a much larger puzzle. Protecting sensitive information requires a multifaceted approach that considers the entire data lifecycle, from collection and storage to transmission and eventual disposal. This necessitates a shift in mindset, moving beyond simply encrypting data to encompass a broader range of security measures.
Effective data protection necessitates a proactive, rather than reactive, approach. This involves implementing robust security policies and procedures that are consistently reinforced and updated to reflect evolving threats and vulnerabilities. Organizations must invest in training programs to educate employees about the importance of data security and the potential consequences of negligence or malicious activity.
Understanding the Threat Landscape
The digital landscape is constantly evolving, and with it, the sophistication and frequency of cyberattacks. Understanding the current threat landscape, including emerging malware, phishing techniques, and social engineering tactics, is critical for developing effective security strategies. Organizations must stay ahead of the curve by continuously monitoring and adapting to these evolving threats.
Cybercriminals are becoming increasingly resourceful and sophisticated in their methods, exploiting vulnerabilities to gain unauthorized access to sensitive data. Organizations need to remain vigilant and proactive in their security measures to mitigate potential risks and protect their valuable information assets.
Implementing Multi-Layered Security
A single layer of security is often insufficient to protect against the complex array of threats in today's digital environment. Implementing multi-layered security measures, encompassing technical controls, administrative procedures, and physical security, is vital for a robust defense strategy. This approach ensures a layered defense, making it significantly harder for attackers to penetrate the security perimeter.
A comprehensive security strategy should include firewalls, intrusion detection systems, and robust access controls. These measures, when combined with strong password policies and regular security audits, create a formidable barrier against unauthorized access and data breaches.
The Human Element in Security
Technology is only part of the equation. Humans are often the weakest link in a security chain. Security awareness training programs, fostering a culture of security, and establishing clear lines of responsibility are crucial to mitigate the risks associated with human error or malicious intent. Regular training sessions and simulated phishing exercises are essential for reinforcing good security practices among employees.
Security breaches often stem from seemingly minor human errors, such as clicking on malicious links or using weak passwords. Cultivating a security-conscious culture within an organization significantly reduces the likelihood of such incidents and strengthens the overall security posture.
Data Loss Prevention and Incident Response
Proactive measures are crucial, but having a robust plan for responding to data breaches or other security incidents is equally vital. Effective data loss prevention strategies are essential to minimize the impact of a security breach. This includes implementing data loss prevention (DLP) tools and technologies to monitor and control sensitive data throughout its lifecycle. Having a well-defined incident response plan in place is essential to minimize damage and ensure a swift and coordinated response to any security incident.
Establishing clear communication channels, protocols, and roles within an incident response team is vital for effective mitigation and recovery. Rapid identification, containment, eradication, recovery, and post-incident analysis are all critical components of a successful incident response plan.