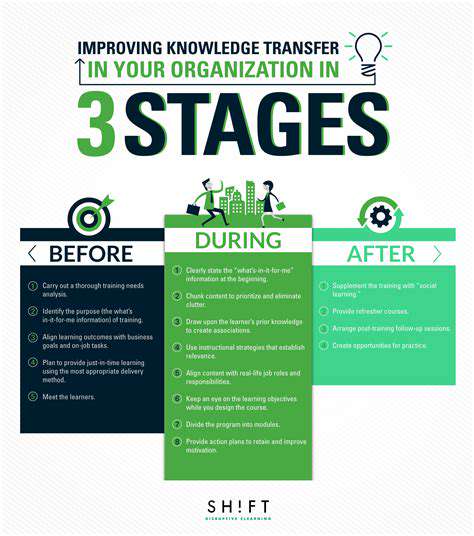
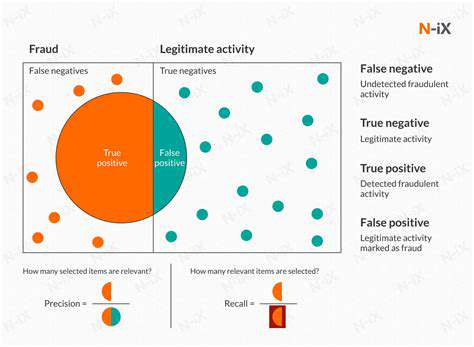
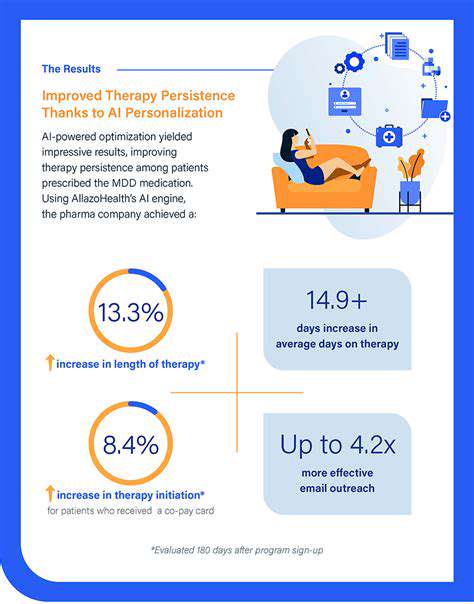
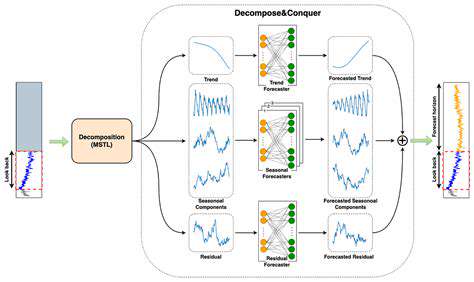
Beyond Key Distribution: Exploring Advanced Applications

Exploring Advanced Encryption Techniques
Beyond the fundamental concept of key distribution, numerous Advanced encryption techniques have emerged to address the complexities and vulnerabilities inherent in traditional approaches. These methods often incorporate intricate mathematical algorithms and cryptographic protocols to enhance security and resilience against sophisticated attacks. Understanding these advancements is crucial for maintaining data integrity and confidentiality in today's digital landscape. Modern encryption often involves the use of asymmetric cryptography, which leverages different keys for encryption and decryption, thereby increasing the complexity and security of the process.
One significant area of advancement lies in the development of quantum-resistant algorithms. As quantum computing technology progresses, current encryption methods may become vulnerable. Consequently, researchers are actively developing and evaluating new cryptographic primitives that can withstand attacks from quantum computers. This proactive approach is essential to ensure the long-term security of sensitive information.
The Role of Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI) plays a vital role in managing and distributing cryptographic keys in a secure manner. It provides a framework for establishing trust and verifying the authenticity of digital identities. PKI relies on a hierarchical structure of trusted entities, including Certificate Authorities (CAs), to issue and manage digital certificates. These certificates act as digital passports, verifying the identity of individuals or organizations participating in online transactions.
Implementing a robust PKI system involves careful consideration of security protocols and the management of cryptographic keys. A well-designed PKI can significantly enhance the security posture of an organization by mitigating the risks associated with key compromise and impersonation.
Advanced Cryptographic Protocols
Beyond PKI, advanced cryptographic protocols like TLS (Transport Layer Security) and SSH (Secure Shell) play a critical role in securing communication channels. These protocols establish secure connections between systems, ensuring that data transmitted over networks remains confidential and unaltered. The protocols employ complex algorithms and mechanisms to authenticate users and encrypt data in transit.
The ongoing evolution of these protocols is essential to maintain security against emerging threats. Regular updates and improvements to cryptographic protocols are crucial for mitigating vulnerabilities and adapting to advancements in attack techniques.
The Future of Encryption
The future of encryption is intertwined with advancements in both hardware and software. As computing power increases, the need for more robust and efficient encryption methods becomes paramount. New research and development in post-quantum cryptography are paving the way for encryption systems resilient to quantum computing attacks. This is critical for safeguarding sensitive information in the face of potential future threats.
Furthermore, the integration of encryption into emerging technologies, such as the Internet of Things (IoT) and blockchain, demands innovative solutions to address specific security challenges presented by these technologies.
The Future of Quantum Cryptography: A Glimpse Ahead
Quantum Key Distribution (QKD): A Secure Foundation
Quantum Key Distribution (QKD) is a revolutionary approach to cryptography, leveraging the principles of quantum mechanics to create unbreakable encryption keys. This method ensures the absolute security of communication channels by exploiting the fundamental laws of physics. QKD's inherent security stems from the fact that any attempt to intercept the key will inevitably disturb the quantum state, alerting the legitimate parties to the intrusion.
Quantum Entanglement: The Cornerstone of QKD
Quantum entanglement is a bizarre yet crucial phenomenon in quantum mechanics. Two entangled particles, regardless of the distance separating them, share an inherent connection. A change in the state of one particle instantaneously affects the state of the other. QKD harnesses this entanglement to generate and distribute secure cryptographic keys, making it exceptionally resistant to eavesdropping.
Challenges in Practical Implementation
While the theoretical underpinnings of QKD are robust, practical implementation faces significant hurdles. Maintaining the delicate quantum states during transmission, particularly over long distances, presents a considerable challenge. The need for sophisticated and expensive quantum devices also limits widespread adoption.
Technological Advancements in QKD
Ongoing research and development in quantum technology are steadily pushing the boundaries of QKD. Improvements in photon sources, detectors, and quantum repeaters are making long-distance QKD more feasible and practical. This progress is crucial for implementing QKD in real-world scenarios, like secure data transmission across continents.
Applications Beyond Secure Communication
The potential of quantum cryptography extends beyond secure communication. QKD's principles could revolutionize various fields, from secure data storage to secure voting systems. The implications for sensitive information handling in various sectors are immense, offering a new paradigm of security and trust.
Security in the Quantum Era
The rise of quantum computing poses a significant threat to current cryptographic systems. However, quantum cryptography offers a resilient solution, ensuring security in the face of advancements in quantum computing. This makes QKD a vital component in building a secure future, safeguarding sensitive information in a rapidly evolving technological landscape.
The Future of QKD: Integration and Scalability
The future of quantum cryptography lies in its seamless integration into existing communication infrastructure and scalability to meet growing demands. Future research focuses on developing more robust and accessible QKD systems, enabling wider adoption and implementation in various sectors, from finance and healthcare to government communications. This will pave the way for a secure quantum-enabled future.